DevBlog #7 - VM's VIFs network traffic control in XO
A new exciting feature is coming to XO's SDN Controller plugin: Controlling VM's network traffic by adding routing rules to a VM network interface!

An exciting new feature will soon be released: controlling the VM's network traffic via XO's SDN Controller. Very soon you'll be able to enable/disable traffic on a specific VM network interface.
How does it work?
This feature is implemented thanks to the OpenFlow v1.1 protocol: an OpenFlow controller, in XO's SDN Controller plugin, sends OpenFlow messages to a XCP-ng's OpenVSwitch (virtual switch managing the traffic for the host and its VMs).
An OpenFlow message allows the controller to add/modify/delete traffic routing rules, this is how we can enable or disable part of the traffic on a VM VIF.
Taking control of OpenVSwitch
OpenvSwitch is the virtual switch of an XCP-ng host, it can have a manager and a controller. The manager will use OVSDB to manage the switch bridges, ports and interfaces, the controller will control the traffic thanks to OpenFlow messages.
The plugin needs to do both, here's how it's done:
- Becoming the SDN controller of the host thanks to XAPI:
xe sdn-controller-introduce protocol=pssl, we usepsslto allow many controllers at the same time as long as teir certificate match the same ca-certificate installed on the host. This allow the plugin to send OVSDB commands to OpenVSwitch. - Becoming the manager of OpenVSwitch bridges thanks to OVSDB: A OVSDB command is send by the plugin to insert our plugin as manager for each bridges of OpenVSwitch. Now the plugin can send OpenFlow messages.
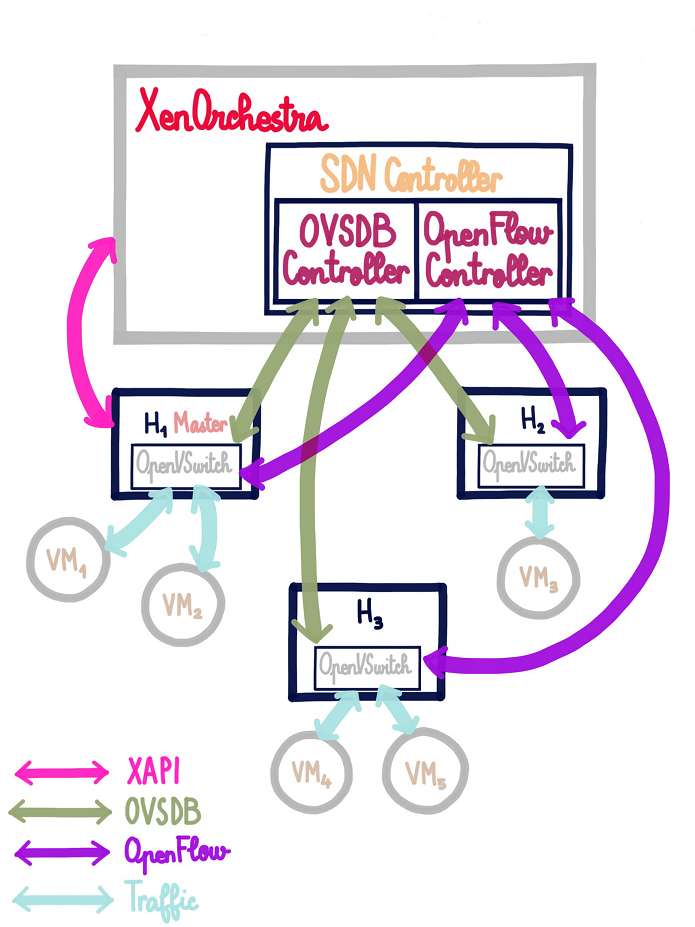
The need for OVSDB is the reason this feature is added to the SDN Controller plugin instead of a new one, the OVSDB protocol was already immplemented for private networks creation in it.
Controlling the traffic
Once the plugin has control over the host's OpenVSwitch its time to control the traffic by sending OpenFlow messages giving rules to apply for specific parts of the traffic to OpenVswitch.
Here's an example of an OpenFlow rule:
priority=65527,tcp,in_port=4,dl_src=ae:f7:4b:84:6c:8b,nw_src=192.168.5.242,nw_dst=192.168.5.55,tp_dst=5060 actions=drop
This means to drop any traffic matching all the following conditions:
- Traffic is TCP on port 5060 (so SIP traffic)
- Traffic comes from the VIF with MAC address: ae:f7:4b:84:6c:8b and IP address: 192.168.5.242
- Traffic goes to IP address: 192.168.5.55
In a nutshell, SIP traffic from 192.168.5.242 to 192.168.5.55 is disabled.
How does the feature look like?
In the VM network tab of XO, a new column has been added to the VIF list: this column allows to view the existing rules and to add one.
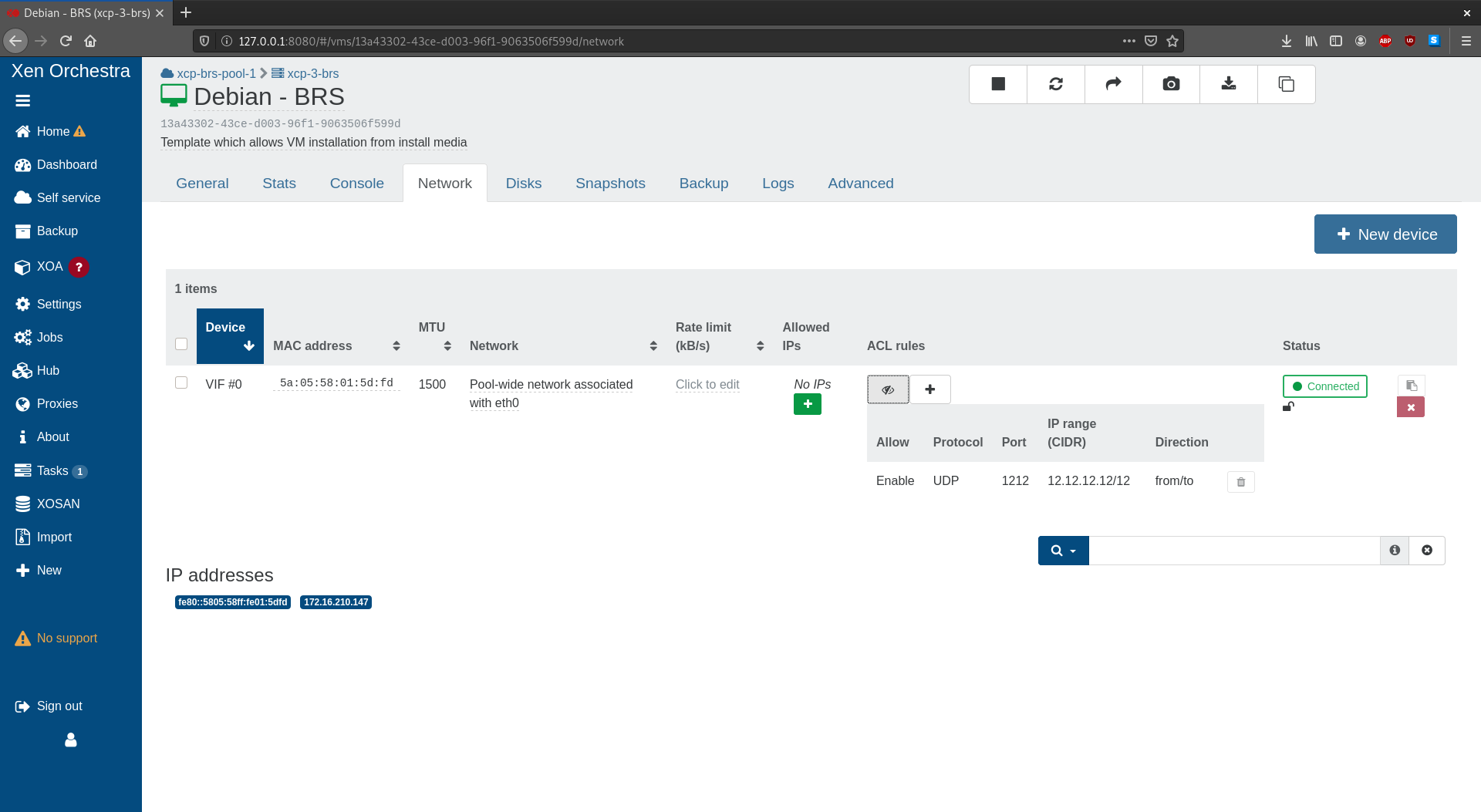
When adding a rule, you can choose to:
- enable/disable the traffic
- for a specific protocol (optional)
- on a specific port (optional)
- for a specific IP or IP range (optional)
- outgoing from the VIF / incoming to the VIF/ both
For instance:
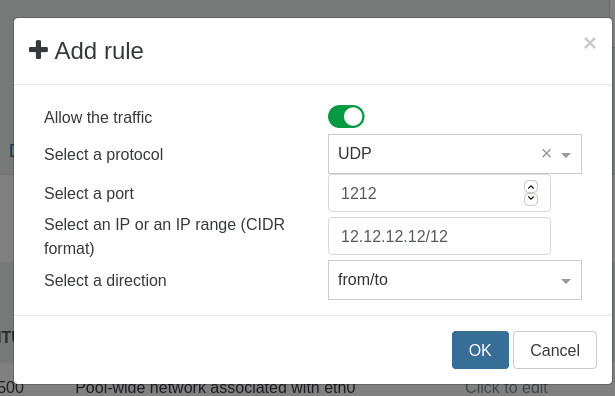
Adding this rule would allow UDP traffic on port 1212 ougoing to and incoming from all IPs in range 12.12.12.12/12 on the selected VIF.
Access the feature
The feature will be released with version 1.0.0 of the SDN Controller (coming soon!). An XCP-ng update will be provided as well for XCP-ng 8.X, it will open the OpenFlow port (TCP 6653) when a SDN Controller is set and close it when there's not:
yum update xapi-core xapi-doc xapi-tests xapi-xe --enablerepo=xcp-ng-testing
Older versions
On a version of XCP-ng older than 8.0, the following command will open the OpenFlow port:
iptables -A xapi-INPUT -p tcp -m conntrack --ctstate NEW -m tcp --dport 6653 -j ACCEPT
Under the hood
For our own requirements, we had to build a JS library from scratch, because any other we found were at least very incomplete or simply broken.
Here is the code: https://github.com/vatesfr/xen-orchestra/tree/master/@xen-orchestra/openflow
If you are interested to get it available in a dedicated repo (eg for your own project), let us know!
What's next?
More rule levels
For now rule can only be applied to a VIF, in the future (probaly with XO6 new design) rule could be added to more levels (VM, Network, Pool, All pools) to have more complex set of rules.
More protocols pre-configured
At the moment the pre-configured protocol are: IP, ARP, ICMP, UDP and TCP. More protocol can be added to ease the use instead of having to specify the port.
For instance:
- HTTP: TCP on port 80
- HTTPS: TCP on port 443
- SIP: TCP on port 5060
- etc