Xen Orchestra 5.111
Xen Orchestra 5.111 is out! This release brings key security improvements, smoother backup and UI experiences, deeper XOA integrations, and new DevOps tools to keep your infrastructure efficient and secure.

September is always that “back-to-school” month in Europe: summer slows down, then everything hits full speed again. This year was no exception: new partnerships, a brand-new security process, and a marathon of events worldwide. And in the middle of all that, we’re shipping XO 5.111, packed with practical updates: Core UI refinements, backup improvements, EasyVirt integration in XOA, REST API progress, and fresh docs to guide you through it all. Let’s jump in!
👨🚀 Project & Community
Let’s start with what’s been happening around Vates, our partners, and the community before diving into the release itself.
Vates + Eviden: Advanced Virtualization Alliance
We’re excited to announce our new partnership with Eviden, bringing serious hardware power into the Vates ecosystem.

The Bull Sequana SH range is now validated with the fully open-source Vates VMS stack—including massive multi-socket servers scaling up to 8 CPU sockets and 960 vCPUs.
For those who like to push infrastructure to its limits, this means you can now combine enterprise-grade hardware with a transparent, sovereign virtualization platform—without compromise.
EasyVirt Integration: DC Scope & NetScope

Just five months after announcing our collaboration with Easyvirt, we’re excited to share that the first milestone of this integration is complete. You can now deploy both DCSCOPE and DCNETSCOPE directly from your Xen Orchestra appliance, and even purchase the Easyvirt suite as an add-on to your Vates VMS subscription.

You can read more on how to deploy it in the dedicated section below.
VSA: a new global security process
We’re introducing a unified process for security: Vates Security Advisories (VSA). From now on, all advisories will be centralized under the VSA system, giving you a single, reliable source to track issues, impacts, and fixes across the entire Vates stack.
A VSA is an official Vates document that includes:
- The nature of a security issue
- Which Vates products and versions are affected
- The severity and potential impact
- Mitigation steps and resolution status
Each advisory is uniquely identified in the format: VSA-YYYY-NNN (for example: VSA-2025-001).
You can read more about the security process in here. All VSAs are accessible there:

XCP-ng 8.2 LTS reached EoL
If you haven't upgraded yet to XCP-ng 8.3 LTS, now is time to do so, as XCP-ng 8.2 reached its end of life on the 16th of September, 2025, as announced previously. There will be no more bug fixes nor security updates for this release. The currently supported release is XCP-ng 8.3 LTS.

XCP-ng 8.3 various updates
First, an important security fix:

VSA-2025-002. More details at https://docs.vates.tech/security/advisories/2025/vates-sa-2025-002And then, some various improvements:

Don't forget to stay up to date!
Community forum milestone
Huge thanks to our community: we hit a new record in September with 3 million unique visitors on the forum! 🚀

💡 Insights
Here are some recent reflections—our own and from others—that shed light on how we work and where our stack is heading.
Remote, hybrid, office? Yes.
A look at how we work at Vates, from my perspective—maybe you’ll pick up a thing or two along the way 😉

My associate, Nithida, also wrote a complementary article (in French) for a business journal: https://www.cadre-dirigeant-magazine.com/reussir-en-entreprise/travailler-a-distance-ce-que-les-entreprises-peuvent-apprendre/
Buying software is a political act
In this column (in French, but easily translatable in your browser), I explain why supporting European open source is both a technological and a strategic choice, essential for long-term independence.

Best practices for XCP-ng setup
A big thanks to Tom from Lawrence Systems, who shared a comprehensive recap of the entire stack in a dedicated forum thread. It’s a great resource if you want to get your XCP-ng setup right from the start:

VMScape and why Xen dodged it
ETH Zürich’s new VMScape attack hit KVM and VMware, but Xen’s microkernel-like design kept it out of reach. Discover the reasons.

🎫 Events
A new section, regarding events you could have found us, or you might find us in the future.
What's next
Some events you can see us directly in the next weeks or in 2 months tops.
🇫🇷 IP & IPAs (October 2, Orléans, France)
Yann will do a presentation and a demo on XCP-ng and Xen Orchestra! Link to event.
🇫🇷 Volcamp (October 2-3, Clermont-Ferrand, France)
Nath will do a talk dedicated on how to use DevOps tools with the Vates stack.
🇫🇷 DataCore Days (October 6-7, Avignon, France)
I'll be personally there. Details and info can be found on our Vates blog post.
🇦🇪 GITEX Global - Expand North Star (October 13-17, Dubaï, UAE)
We'll have a Vates booth. Come to say hi! https://www.gitex.com/
🇺🇸 KubeCon (November 10-13, Atlanta, USA)
We'll have a booth and we'll have some nice announcement there. https://events.linuxfoundation.org/kubecon-cloudnativecon-north-america/
We've been there
Let's review the main events we've been in this September.
🇺🇸 Xen Summit 2025 (Santa Clara)
I will write a dedicated article about the event, with all our presentation, photos and Youtube replays.


It's still too early now, but keep an eye on the XCP-ng blog. Or wait for the next release in here!
Event URL: https://events.linuxfoundation.org/xen-project-summit
🇩🇪 Qubes OS Summit 2025 (Berlin)
As we have strong commitment in the upstream, we are also discussing security and isolation in a broad way, not just inside the datacenter. That's why we are proud to participate to the Qubes OS Summit.
More on https://events.dasharo.com/event/2/qubes-os-summit-2025
🇳🇴 Security Expo 2025 (Oslo)
It was about Sovereign Private Cloud, and as you can imagine, we've been a good fit there!
More at https://blue-services.nl/evenement/blue-services-security-expo-september-2025/
Pheeewww. We did it! Busy month, right?
XO 5.111
Now let's talk about this new XO release.
🛡️ Security
Unlike previous releases, we'll start with a new section: security.
Npm supply chain attack
Our first VSA was regarding XO. You might have been heard about an npm supply chain attack (npm is the package managed for NodeJS, the engine of Xen Orchestra).
That's why we published a first Vates Security Advisory (VSA) for it, even if we were not impacted (no production dependency was in the list of affected repositories). You can read more details in the VSA:

More on the XO 5.107 security patch
Even if it happened few releases ago, we wanted to make sure everyone is up to speed, if you use our LDAP plugin.
With the Xen Orchestra 5.107 update, we released a subtle but important security patch, without disclosing too many details at the time. Here’s what was happening: prior to XO 5.107, if you were using the LDAP plugin (auth-ldap) and had misconfigured the ID attribute field in its settings (by specifying an attribute name that doesn’t exist in the user schema), then a user A could have been able to log into Xen Orchestra as another user B (potentially even an admin). In some cases, user B’s username might also have been overwritten with user A’s username, resulting in duplicate usernames in the user list.
Although it’s unlikely this issue occurred on your XOA, let alone went unnoticed, we still recommend following these steps:
- Ensure you’re running Xen Orchestra 5.107.0 or later (
auth-ldap0.10.11). - Go to Settings → Users and check for duplicate usernames. If any are found, the account with Admin permissions is most likely the one that needs to be corrected.
- Use the
permission:adminfilter to confirm there are no unexpected users with Admin permissions.
💾 Backup
Since we published our new backup engine, things are going pretty smooth. We are entering a phase of various improvements and fixing details.
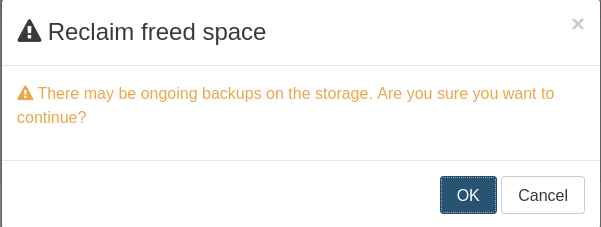
Prevent accidental space reclamation
We’ve added a safety check to the space reclamation process. Because reclaiming freed space during active backups can lead to serious issues, Xen Orchestra will automatically block the operation while backups are running.
If you still need to proceed, you can override the protection using the new confirmation dialog:
🥝 Core UI
Core UI is the next-gen common UI for both XO 6 and XO Lite.
Improved UIcollapsibleList Component
We’ve updated the UIcollapsibleList component across the interface. Previously, the text showing how many extra items were hidden wasn’t clickable—you had to use a separate See all link. Now, you can click directly on the item count to expand the list.
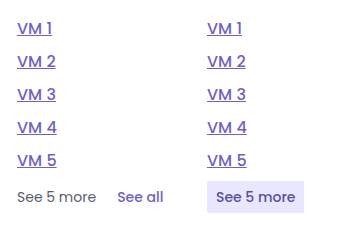
This makes the interaction more straightforward, and the component feels cleaner and more responsive overall.
Updated VM dashboard
We’ve updated the VM dashboard in the core UI to align with our latest designs. The new layout, spacing, and visual elements follow the design specs more closely, which results in a cleaner and more readable interface.
This update doesn’t introduce new functionality, but enhances the overall experience with a more polished and intuitive look.
Error visibility in dashboard cards
Dashboard cards now display an error indicator when the data for a card fails to load. This means you no longer need to sift through logs or secondary views. The problem is flagged right where you’re already looking.
This makes it easier to spot issues quickly and respond without delay.
🛰️ XO 6
Some features of Core UI are exclusive to XO 6, as XO Lite isn't meant to provide all XO features. And this month, it's all about backups!
VM backup jobs table
XO6 now features a dedicated table that lists all backup jobs associated with a specific VM. This makes it easy to see which jobs are protecting the VM and how they’re configured.
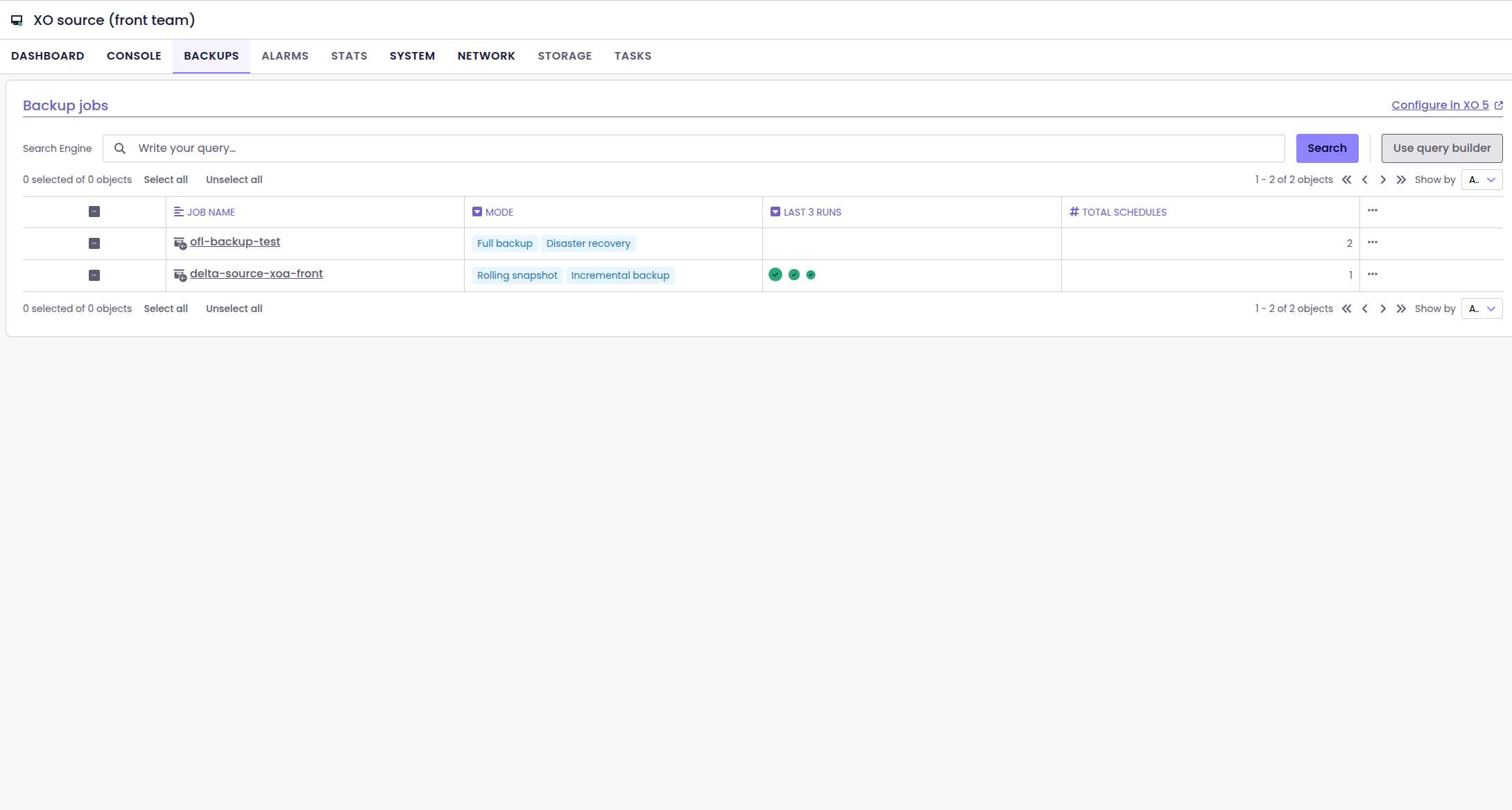
Instead of digging through the global backup view, you can now check everything directly from the VM page, and quickly verify that the right jobs are in place. It’s a small but highly practical improvement for monitoring your backup coverage.
Backup job details in the side panel
Now, as soon as you enter the Backup job view, you can see the backup job details in the side panel. This way, you no longer have to leave the page or open a separate view to get the information.
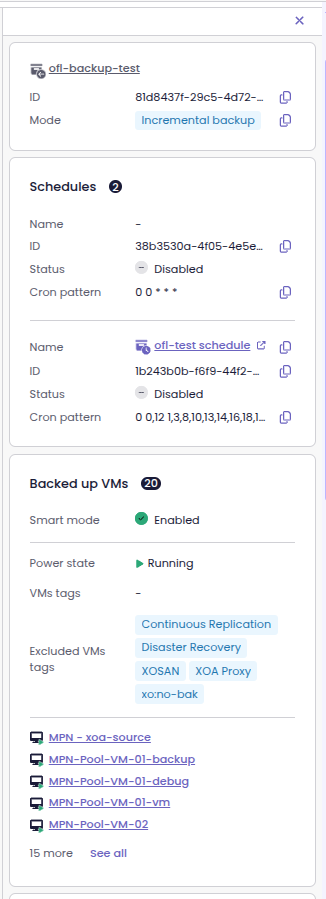
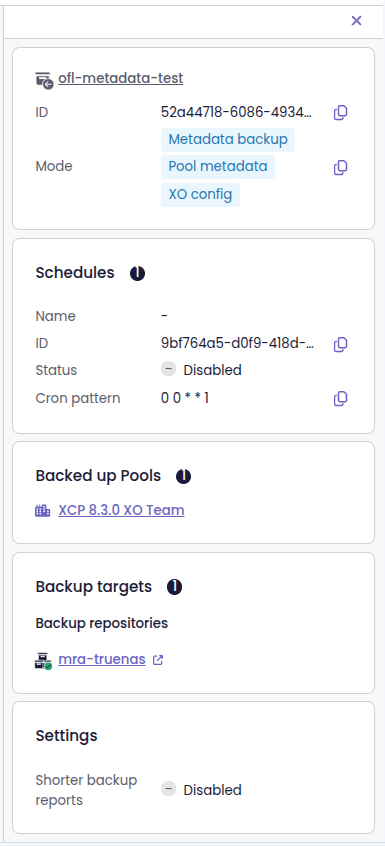
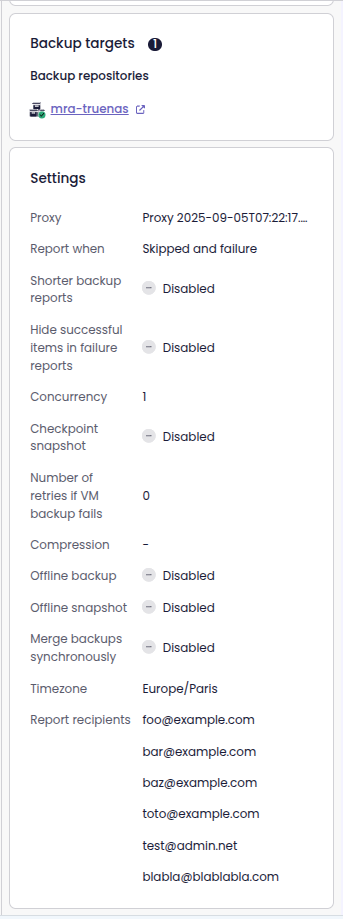
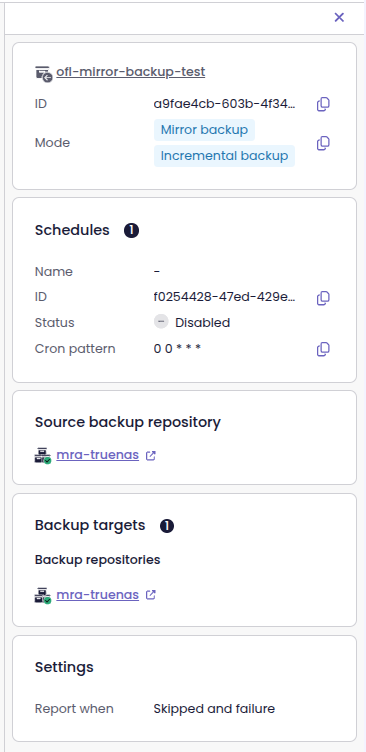
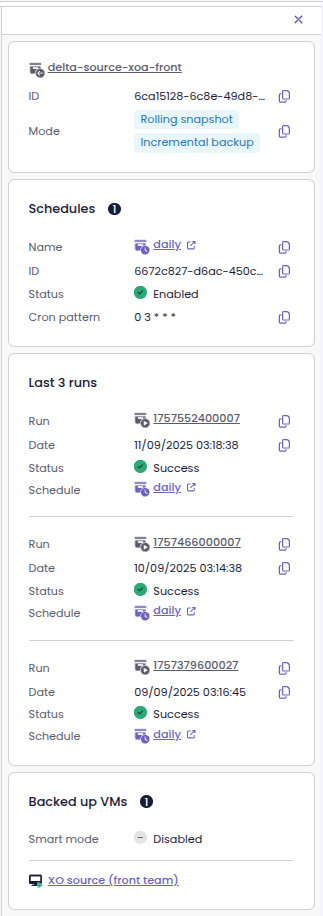
Backup jobs appearing in the side panel
Alarms and patches in dashboards
The dashboards for hosts and VMs now show active alarms front and center. You can see issues immediately, without navigating through multiple screens, so you can respond faster when problems arise.
Also, the host dashboard now includes a dedicated Patches section. You can instantly check applied and missing patches, all without leaving the dashboard.
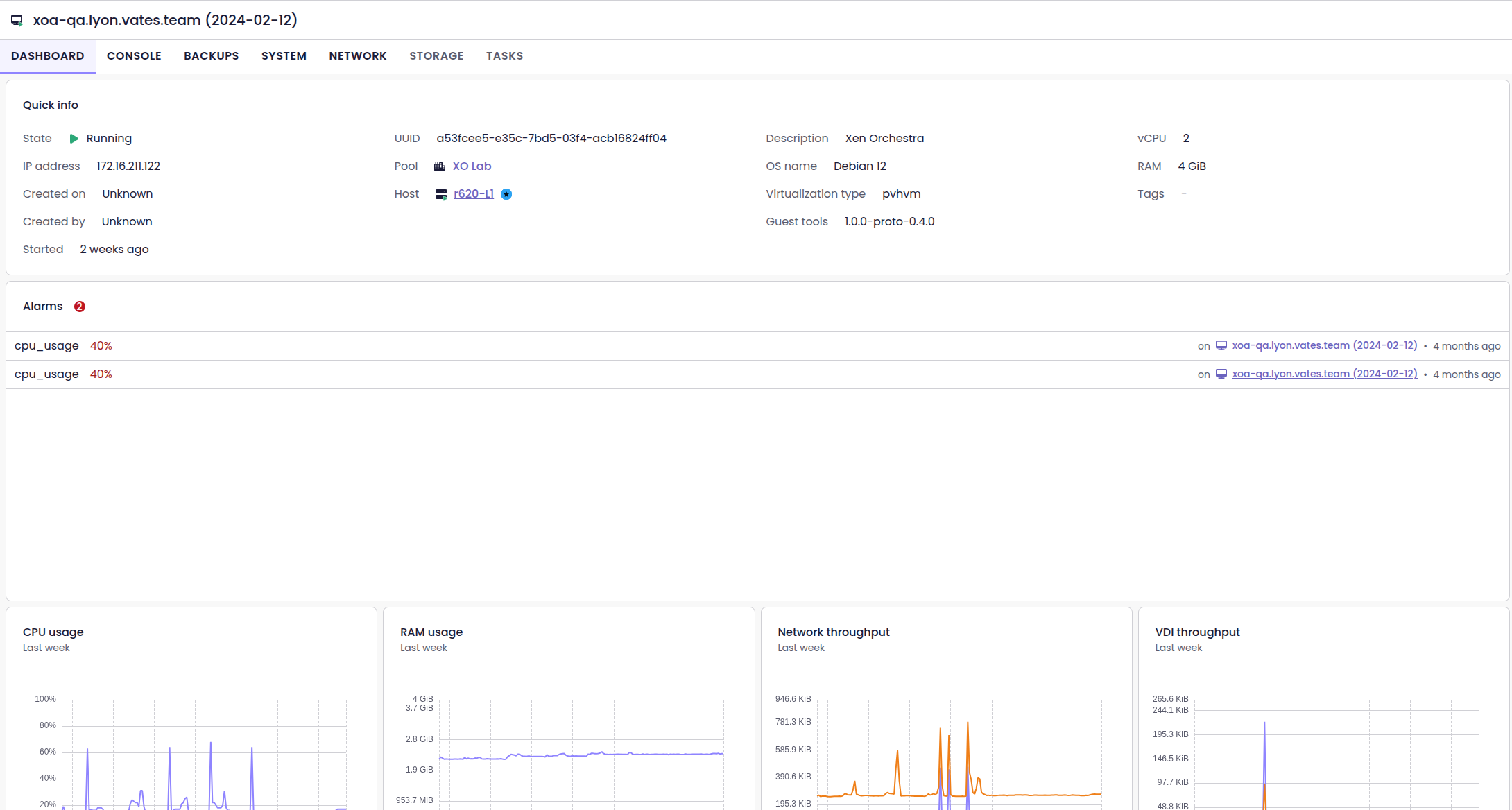
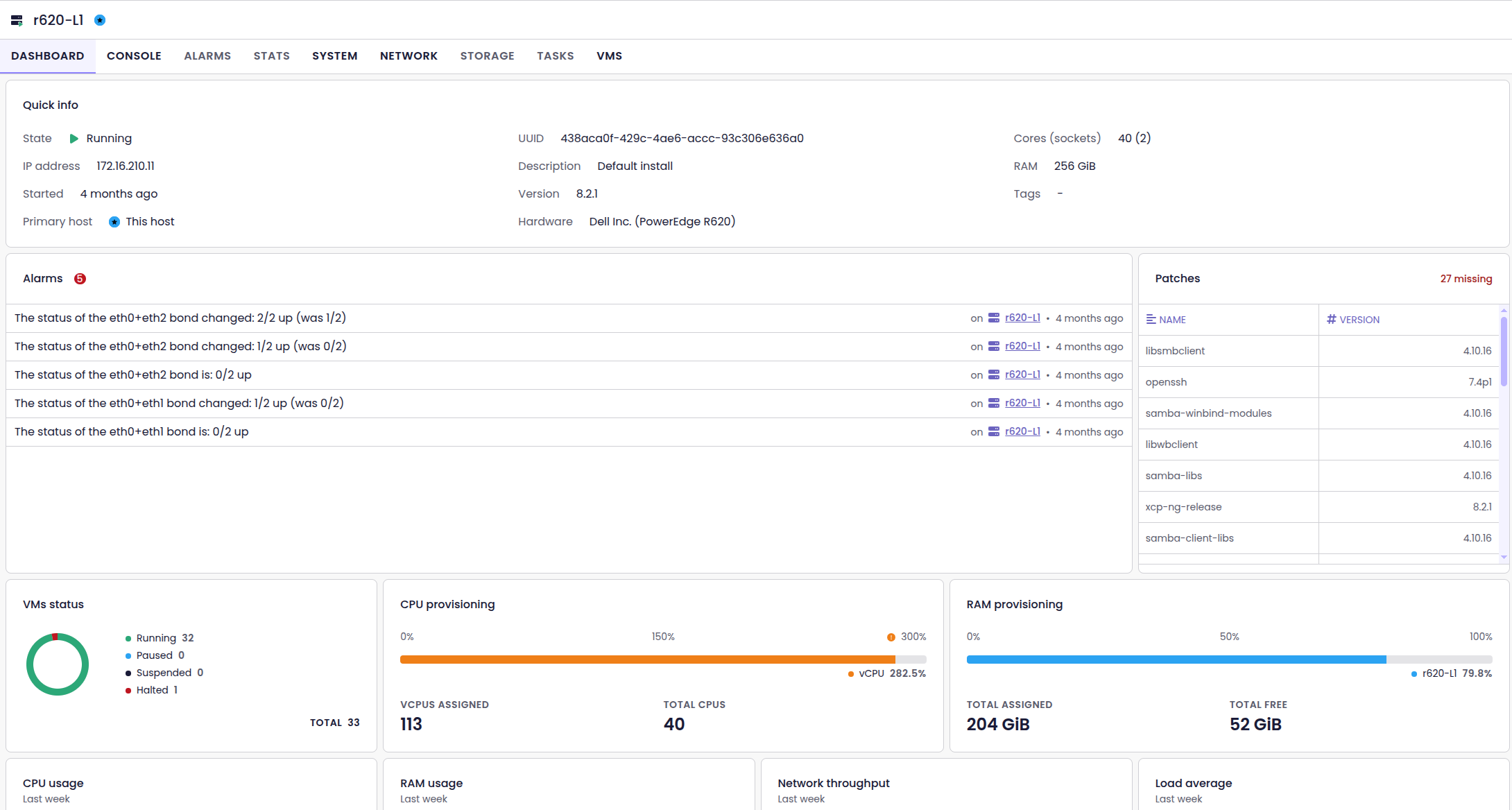
Backup job run list
XO6 has a new Runs page, dedicated to backup jobs. You can now see the history of when and how each backup job has run, if the run has succeeded or failed. In addition, you can also access detailed logs for those jobs.
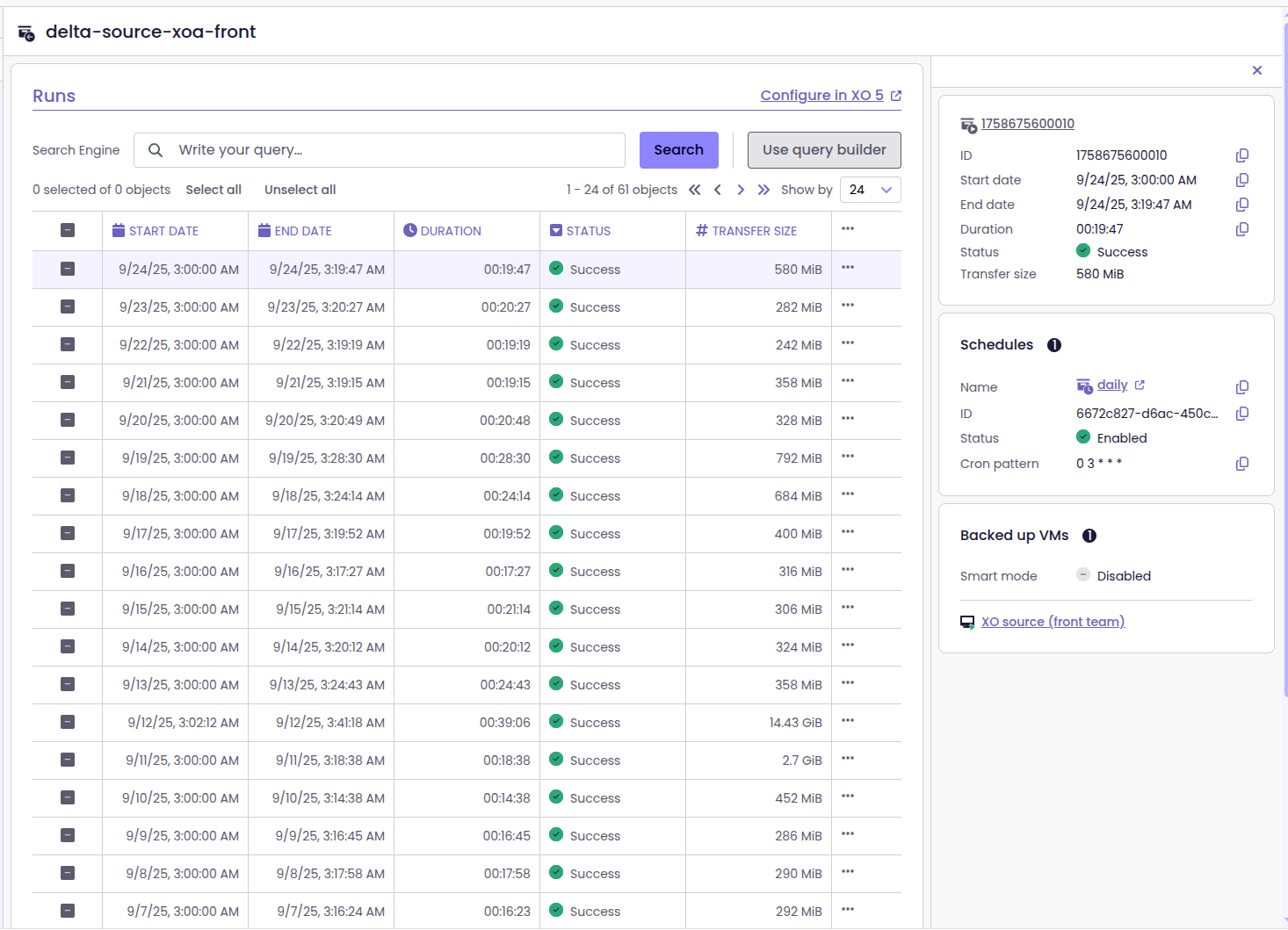
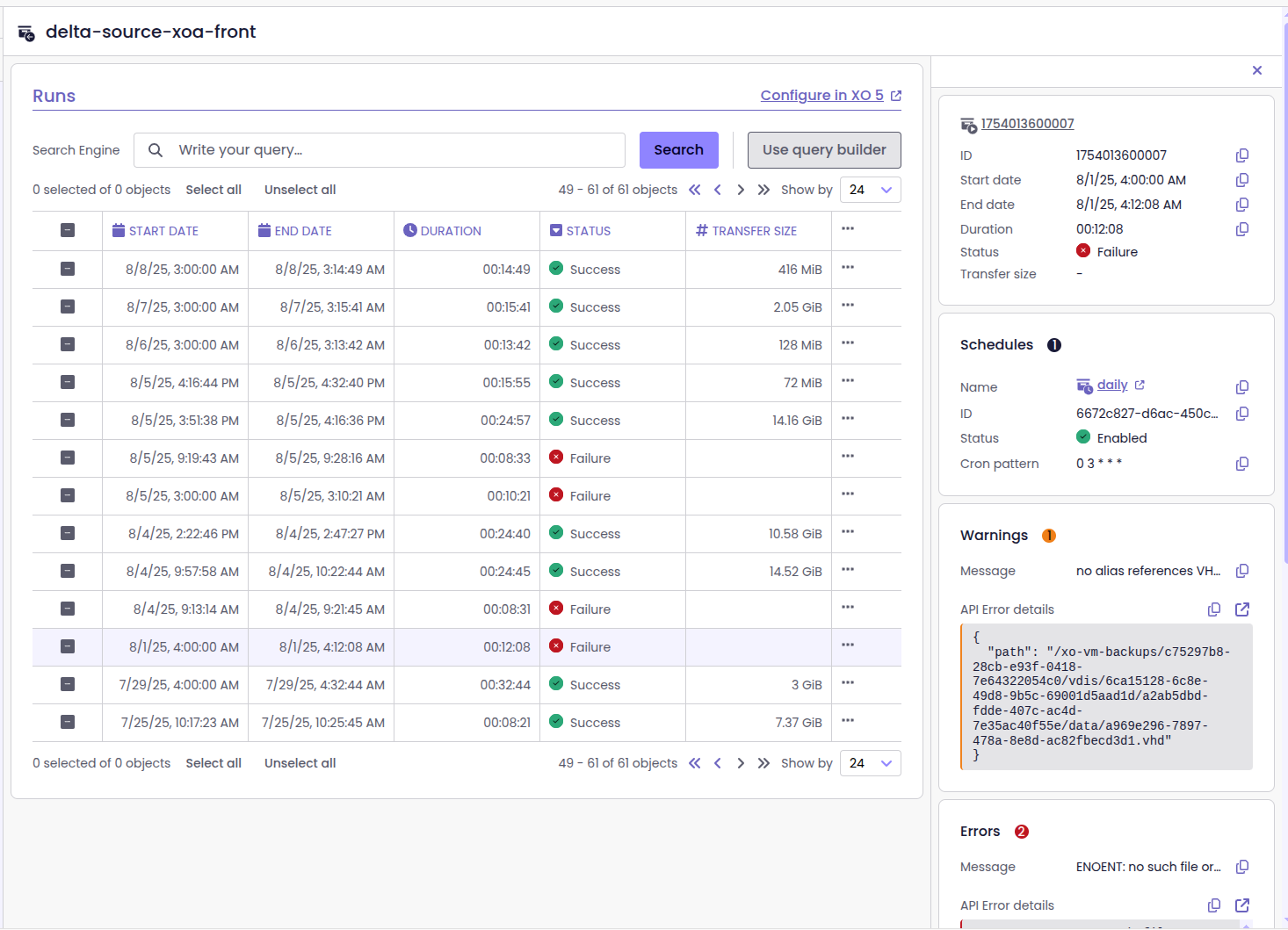
This makes it much easier to monitor backups, identify issues, and verify the protection of your VMs without jumping between screens.
🔭XO Lite
As we are moving forward with Core UI and XO 6, XO Lite is also enjoying new view and features.
Visual indicator for external links
We've made the user experience a little more reliable and consistent, with a little icon that now accompanies all external links. This will clearly signal when the user will navigate outside the application.
External links before the update
External links since the XO 5.111 update
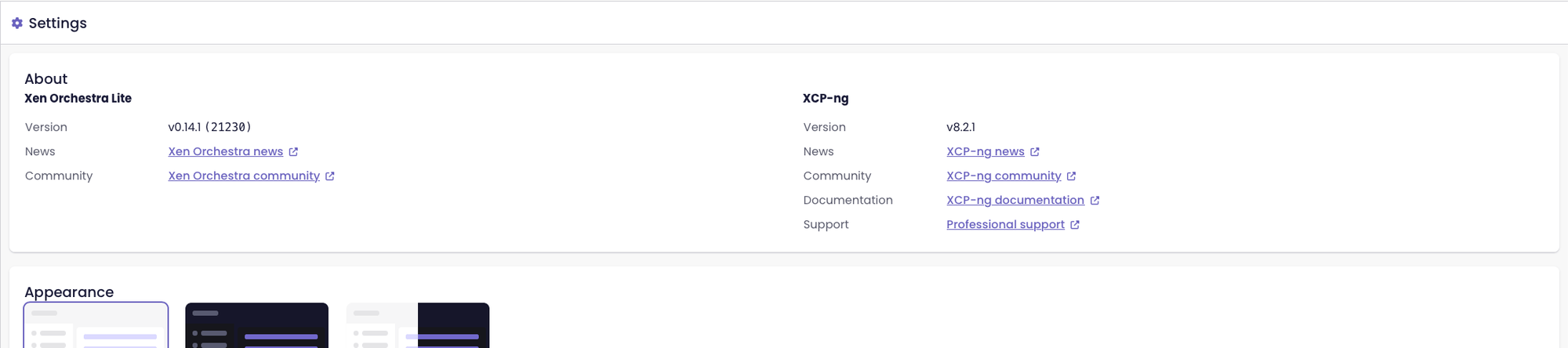
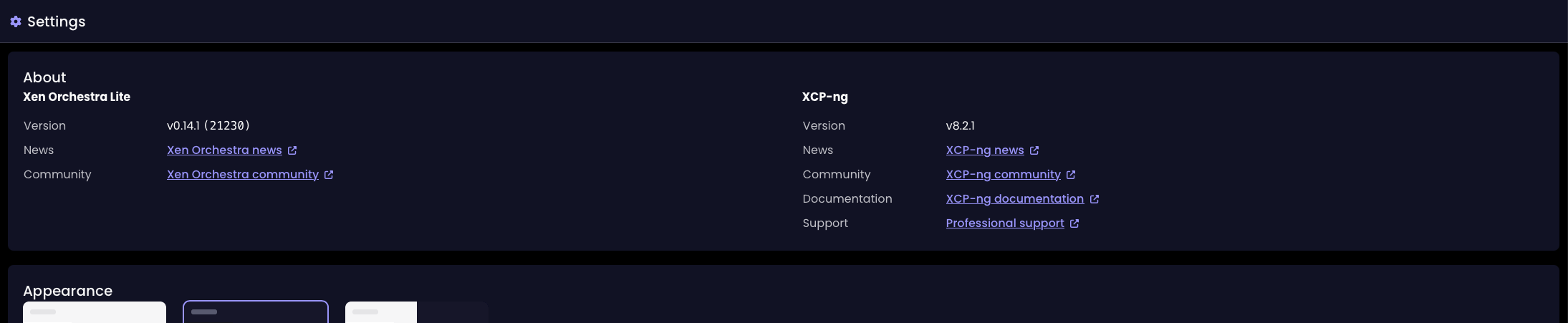
Improved key/value alignment in Settings
The Settings page now shows keys and values aligned naturally, rather than splitting them into separate columns. This small change makes the page easier to read and keeps the layout clean and consistent.
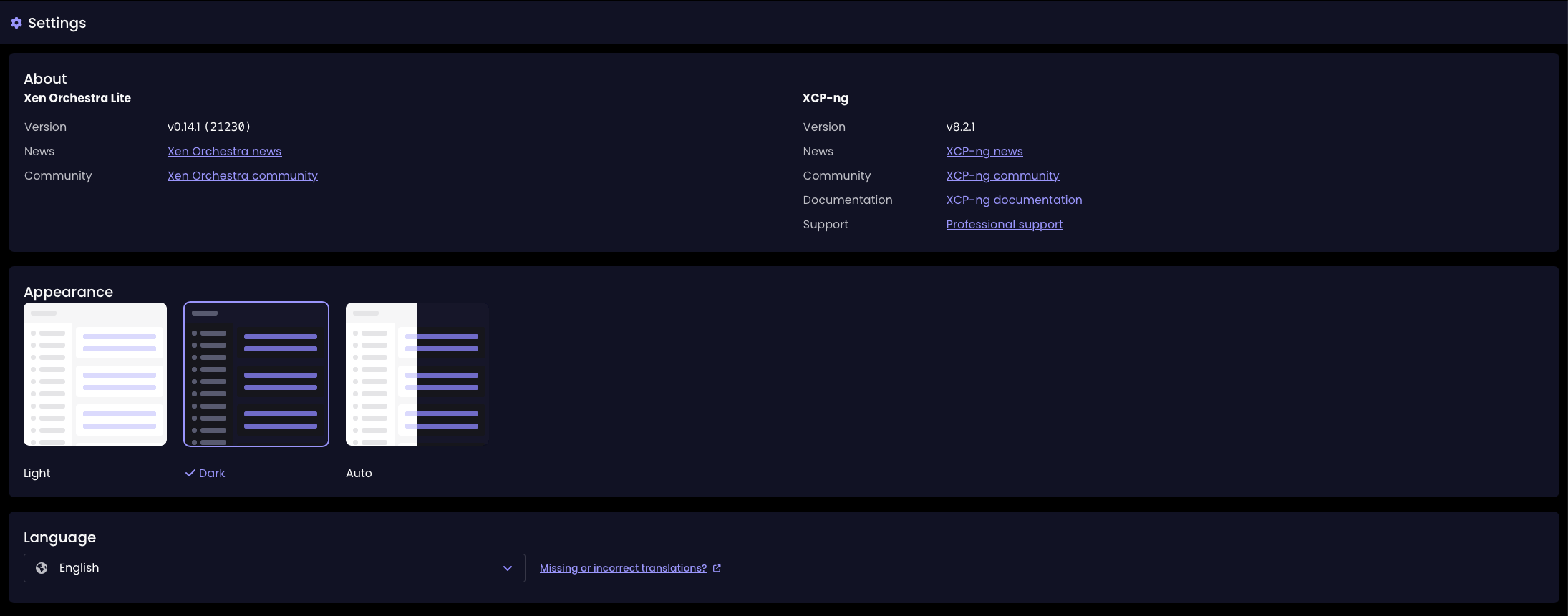
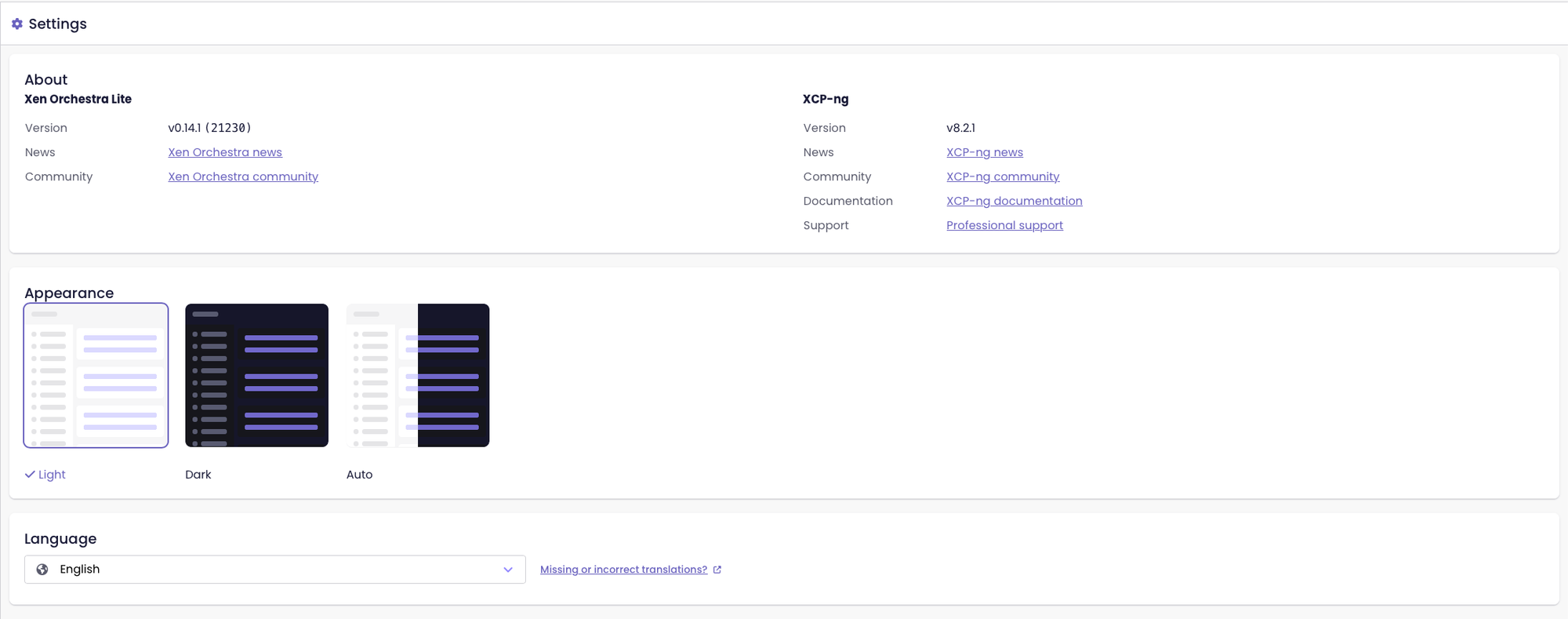
Key/value alignment before the update
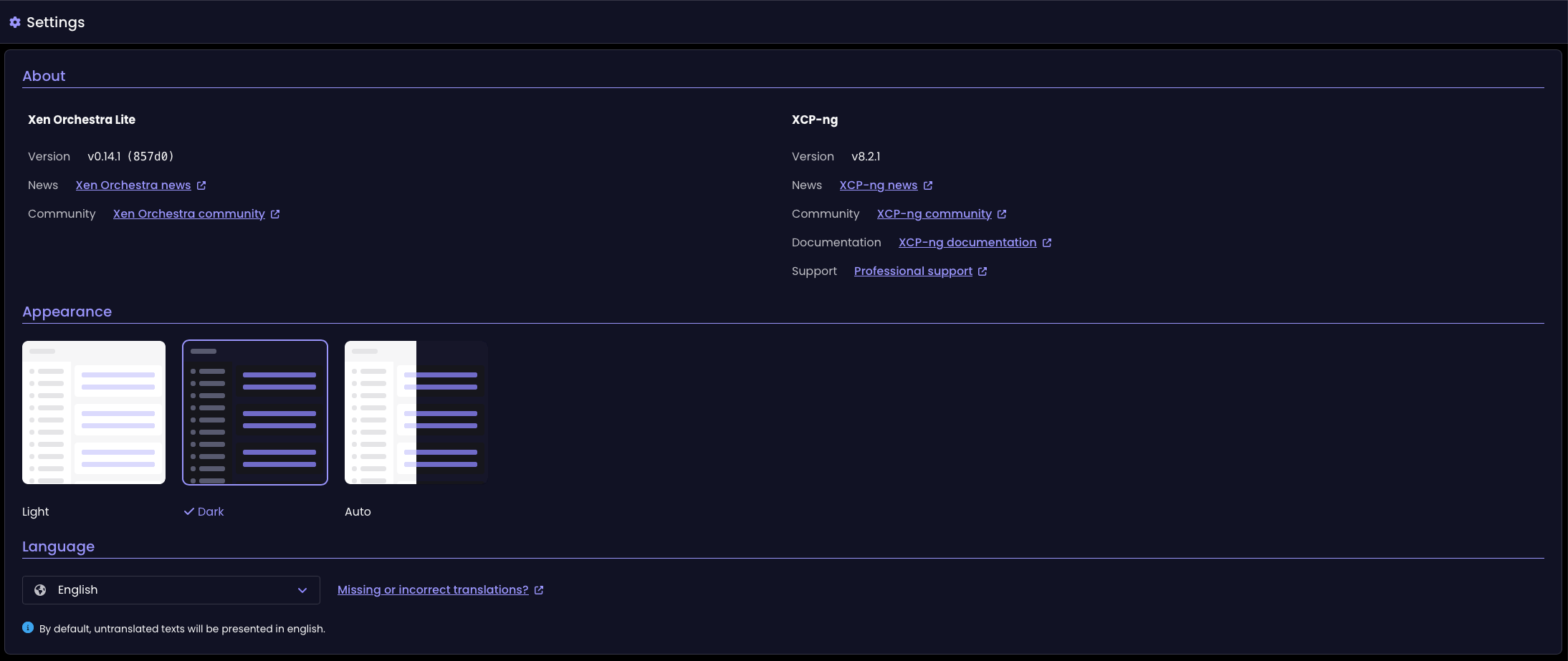
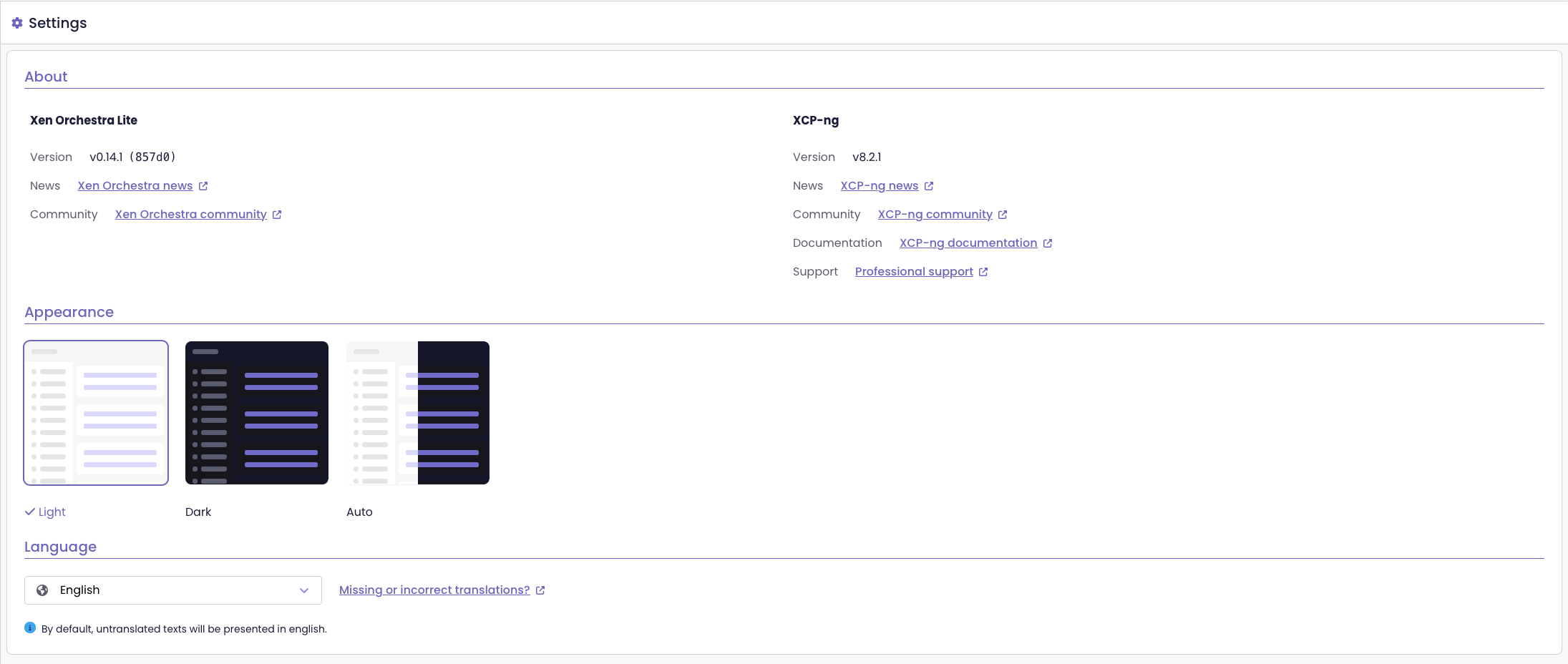
Key/value alignment since the XO 5.111 update
🪐 XOA
This month, we are introducing the capability to deploy a partner solution as if it was a Vates product! If you need capacity planning, energy usage overview or even Network flow analysis, you should try it now!
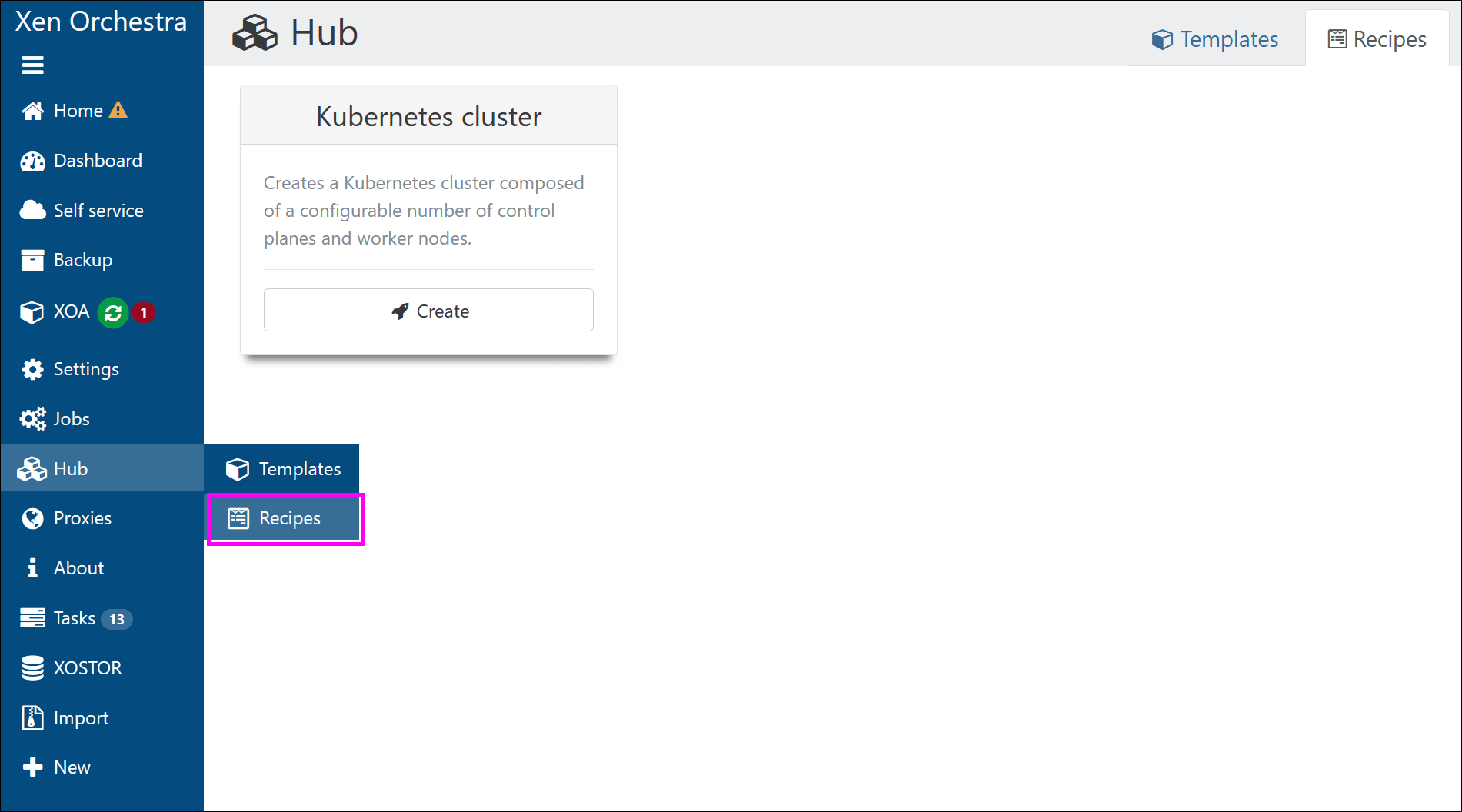
EasyVirt DC Scope and NetScope integration
You can now deploy and access EasyVirt’s DC Scope and DC NetScope tools directly from Xen Orchestra. The tools open within XO, so you can access their overviews without switching applications.
The deployment forms and overview cards appear in the Recipes view for all users, whether on the free version of Xen Orchestra or XOA:
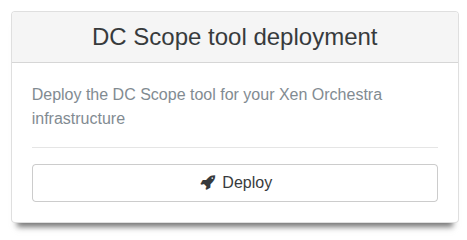
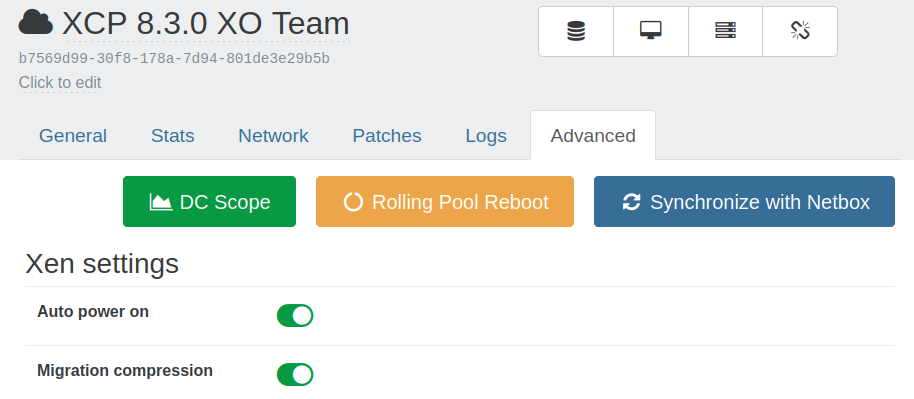
This integration makes it easier to manage, deploy and monitor your infrastructure with EasyVirt’s tools.
📡 REST API
Our REST API is evolving fast, and going to be almost 100% swagger compatible in our next releases.
Deprecated endpoints
Several API endpoints for backups and restores are now deprecated and will be removed in one year.
If your integrations rely on these endpoints, you’ll need to update them before the removal date.
Affected endpoints:
GET /rest/v0/backup/jobs/vmGET /rest/v0/backup/jobs/vm/<backup-job-id>GET /rest/v0/backup/jobs/metadataGET /rest/v0/backup/jobs/metadata/<backup-job-id>GET /rest/v0/backup/jobs/mirrorGET /rest/v0/backup/jobs/mirror/<backup-job-id>GET /rest/v0/backup/logsGET /rest/v0/backup/logs/<backup-log-id>GET /rest/v0/restore/logsGET /rest/v0/restore/logs/<restore-log-id>
What to use instead:
- Replace
/backup/jobs/vm,/backup/jobs/metadata, and/backup/jobs/mirrorwith/rest/v0/backup-jobs. - Replace
/backup/logswith/rest/v0/backup-log. - Replace
/restore/logswith/rest/v0/restore-logs.
Be sure to update your integrations before these endpoints are removed!
Endpoints moved to Swagger
Several existing endpoints have been moved to Swagger. Here's the full list:
DELETE /rest/v0/tasksDELETE /rest/v0/tasks/<task-id>DELETE /rest/v0/vms/<vm-id>DELETE /rest/v0/vm-templates/<vm-template-id>DELETE /rest/v0/vm-snapshots/<vm-snapshot-id>DELETE /rest/v0/vdis/<vdi-id>DELETE /rest/v0/vdi-snapshots/<vdi-snapshot-id>POST /rest/v0/tasks/<task-id>/actions/abortPOST /rest/v0/srs/<sr-id>/vdisGET /rest/v0/vdis/<vdi-id>.(raw|vhd)GET /rest/v0/vdi-snapshots/<vdi-snapshot-id>.(raw|vhd)GET /rest/v0/vms/<vm-id>.(xva|ova)GET /rest/v0/vm-templates/<vm-template-id>.(xva|ova)GET /rest/v0/vm-snapshots/<vm-snapshot-id>.(xva|ova)GET /rest/v0/groups/<group-id>/usersGET /rest/v0/users/<user-id>/groupsGET /rest/v0/users/meGET /rest/v0/users/me/*GET /rest/v0/vms/<vm-id>/messagesGET /rest/v0/users/<user-id>/authentication_tokensGET /rest/v0/vms/<vm-id>/tasksGET /rest/v0/vm-snapshots/<vm-snapshot-id>/messagesGET vm-templates/:id/messages
We've also added brand new endpoints to Swagger: /rest/v0/proxies and/rest/v0/proxies/<proxy-id>
This update makes it easier to test the REST API, and brings us closer to having it fully documented and accessible in Swagger.
For more details on the migration of the API documentation to Swagger, see the initial announcement from the XO 5.104 release:

☸️ DevOps Tools
We continue to move forward on DevOps tools. Getting the initiative and doing it ourselves is a lot of work, for sure, but also the guarantee of the quality level we can bring you, instead of relying only on community maintained plugins or tools.
Terraform Provider is now available in version 0.35.1:
3 bugs fixed making template and VM creation a lot easier. We also worked on the library which is the foundation of our Go providers, the Golang SDK. You can now have more logs by using TF_LOG_PROVIDER=DEBUG.
🐦 VMware to Vates (V2V)
It's been a month since we had our new V2V engine, using VDDK, considerably accelerating the migration, and allowing warm migration. This code is now landing in stable as it was working great!
Don't forget to take a look at our previous announcement for all the details:

As a quick reminder, the performance difference with VDDK is really huge:
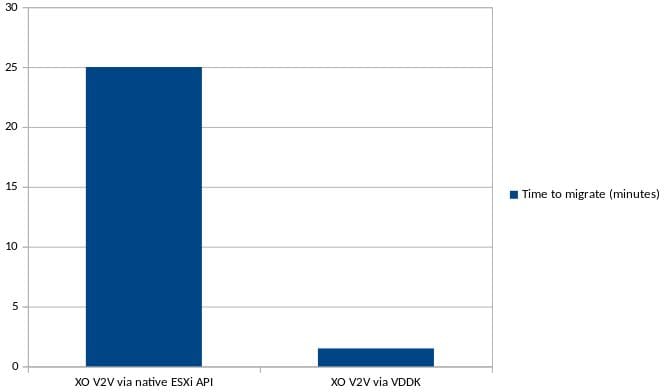
We also vastly improved the documentation on how to migrate from VMware with a brand new detailed V2V guide, see below.
📖 Documentation & guides
Having a good documentation is an important part of doing a good product. That's why we are committed to provide, each month, a recap on the work we are doing regarding the documentation.
Introducing the Vates VMS documentation
We’ve launched a new documentation site for the Vates Virtualization Management Stack (or Vates VMS).
Since our products are deeply interconnected, we needed a centralized resource to cover topics that span across multiple solutions, without tying them to any single product’s documentation.
The site provides a clear overview of our products and services, along with general guides on cross-cutting topics. It’s designed as a starting point for anyone looking to understand what Vates offers, and how our solutions work together. However, it doesn’t replace the existing technical docs for Xen Orchestra or XCP-ng, which are still available at their usual locations.
Some sections are still being filled in, but we’ll continue to expand it over time.
You can check out the Vates VMS documentation here:

Migrating VMs from Vmware
We've published a new guide in the Xen Orchestra documentation! It will help you migrate your VMs from VMware to a Vates stack, without any issues. The guide covers the important steps, good practices and key factors to reduce downtime and make this process as seamless as possible.
The V2V migration guide guide expands our documentation with practical, up-to-date guidance for organizations looking to move away from VMware.

New guide for backup strategies
We just added a guide to the XO documentation, designed to help you formulate a good backup strategy.
It walks you through some of the key decisions, including which backup type to choose and how to determine your retention strategy, so you can keep your data safe and recoverable.
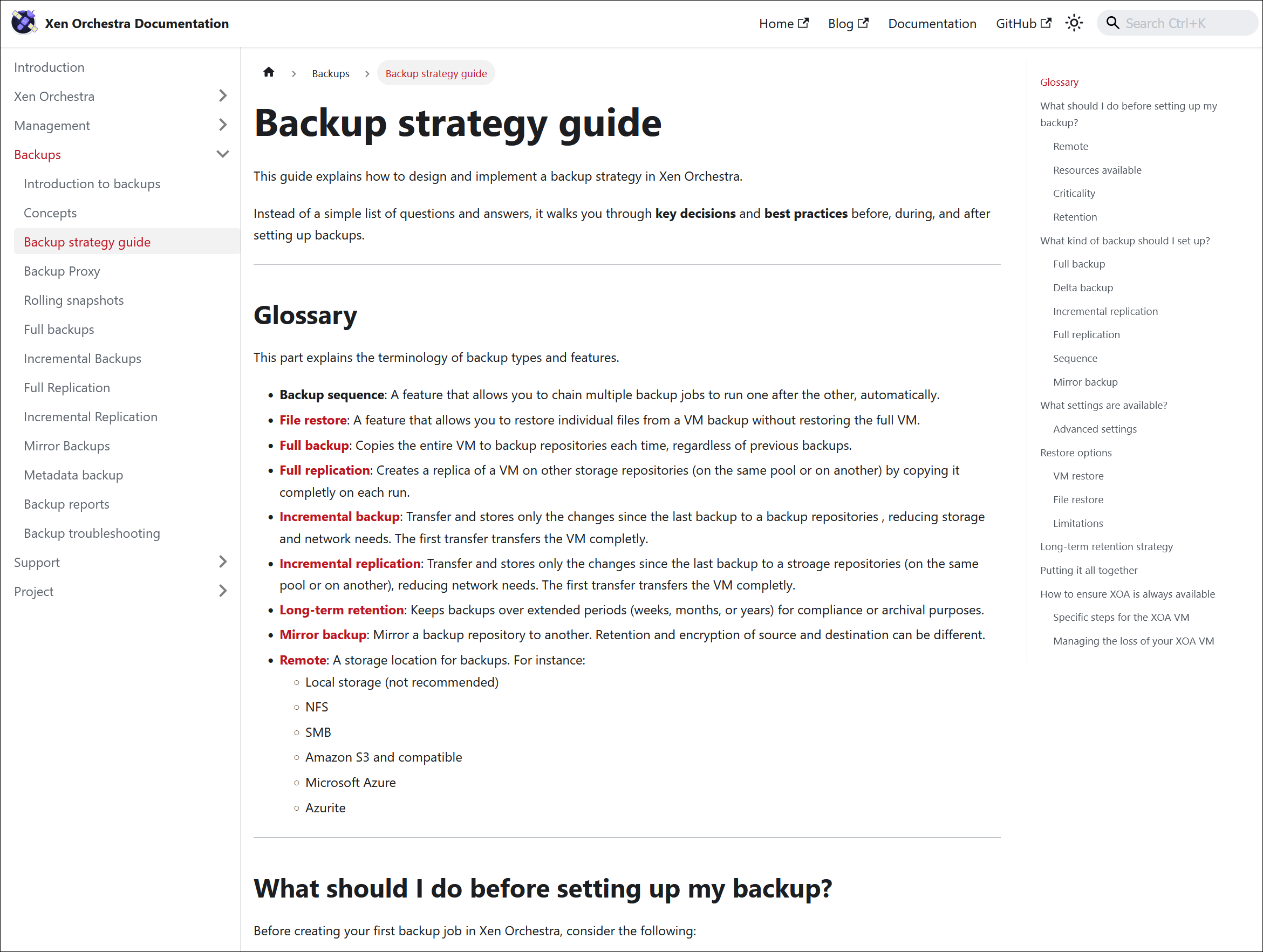
This guide is a practical resource for anyone setting up or reviewing their backup policies. We’ll continue to update and expand it over time, based on feedback and new best practices.

Getting started with Recipes
The Advanced Features page in the Xen Orchestra documentation has a new section dedicated to Recipes. This section explains what Recipes are and what they do (in short: you can use them to automate your VM deployments):

For advanced users, the section also links to the new Vates VMS documentation, where you’ll find a step-by-step guide on using Recipes to deploy a full Kubernetes environment, in just a few clicks:
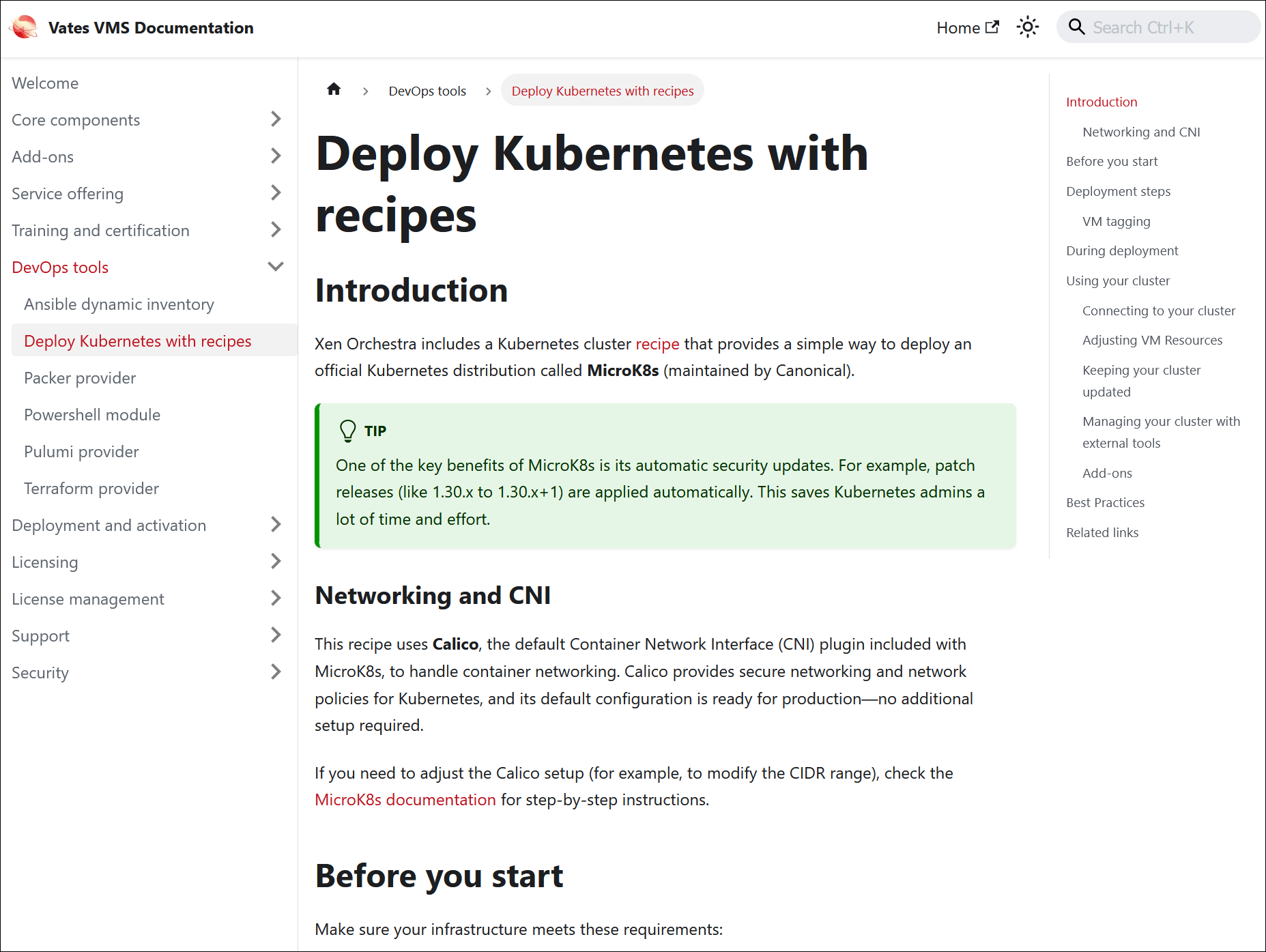
You can access the Kubernetes deployment guide directly, by clicking the link below:
🌐 Translations
It's important for us to have our software translated in many languages as possible, and we do it in a collaborative fashion, thanks to Weblate!
8 languages updated
A big thank you to our community for their ongoing efforts in translating Xen Orchestra!

This month, special attention was given to Czech, Spanish, Italian, Dutch, Brazilian Portuguese, Russian, and Ukrainian.
A special shout-out to Lux_ for also refining the French translation, with better wording for several strings.
Want to help translate Xen Orchestra or improve existing translations? You’re more than welcome to join in here.

🔦 Community spotlight
We had some nice community contribution this month, let's showcase one!
First, maybe you remember our PowerShell module, release few month ago:
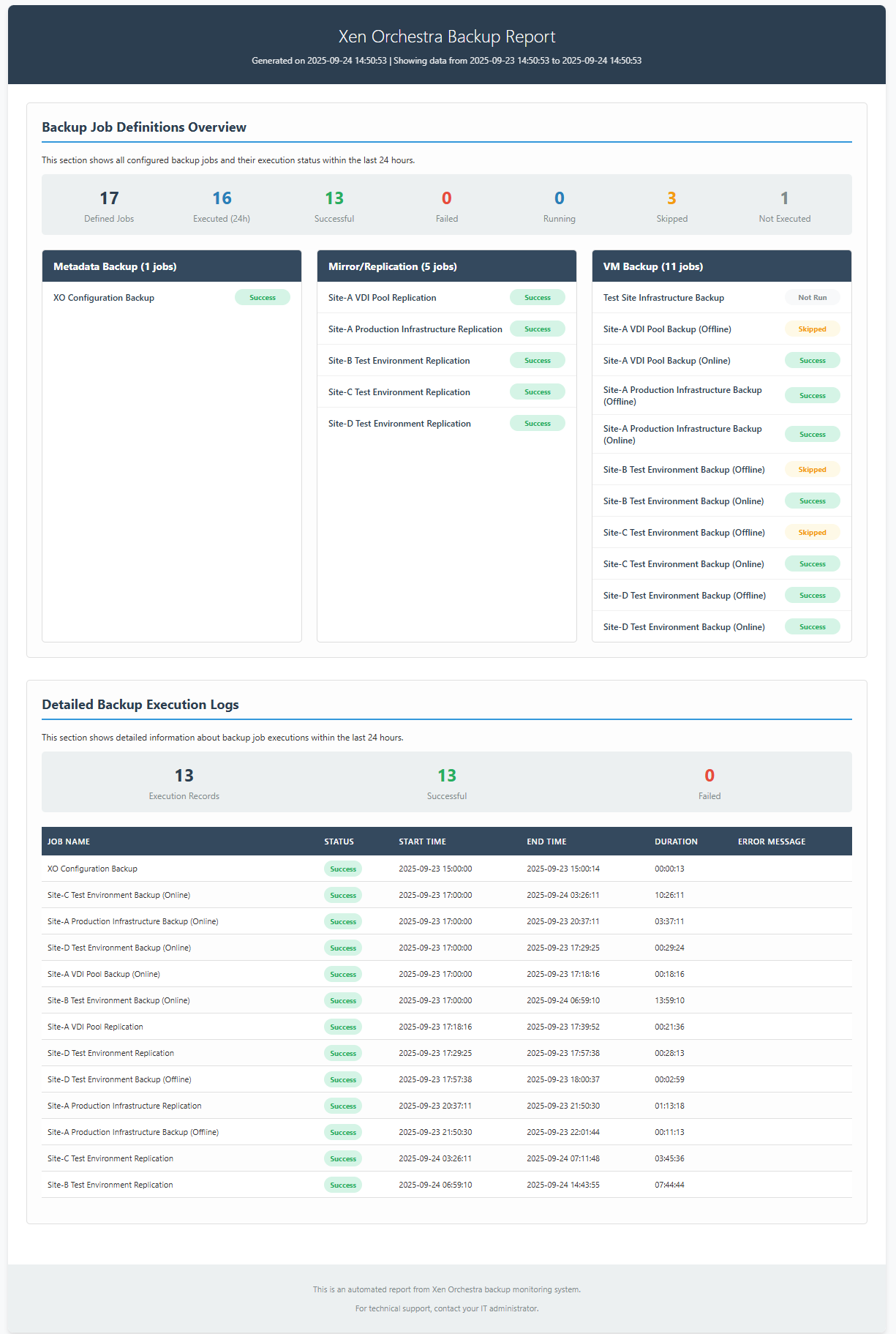
It was a huge success and we have many users now. Some are already building cool things on top of it, for example a script used to do a custom backup report:
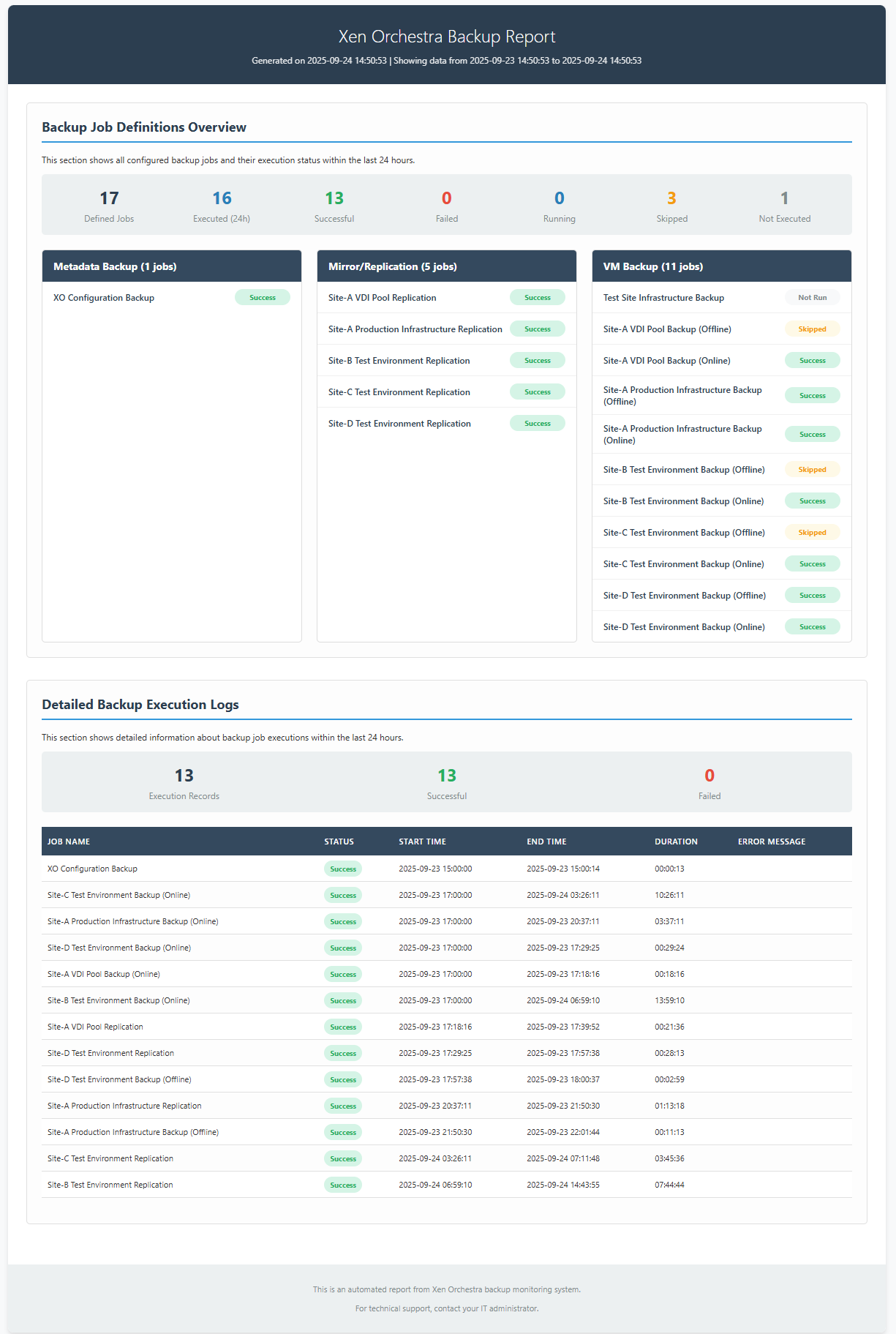
You can find the dedicated thread on our forum and the author, tmk, in here:
🆕 Misc
I know, September is the big "back to school", but still, the sheer size of the "Misc" section deserve a big kudo to the XO team!
SSH keys in CloudConfig templates
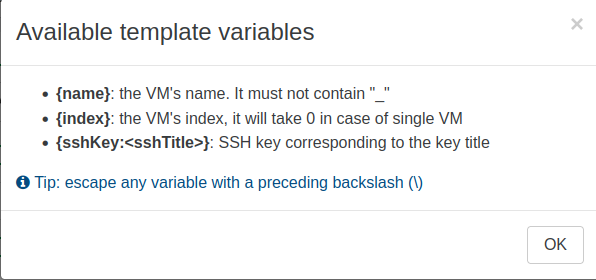
We’ve added a new sshKey variable to Cloud config templates. Previously, you could already inject your public key when launching a VM, but this update simplifies the entire process. You'll no longer have to manage multiple versions of the same template.
It’s a simple way to keep your configuration tidy and ensure secure access right from the start.
Configurable import timeout
You can now set a custom timeout when importing a VM from a URL. This feature was added in response to partner feedback requesting more flexibility for lengthy transfers.
To configure the timeout, use the following parameter:
[jsonrpc-api]
xvaImportFromUrlTimeout = '6s'By adjusting the timeout to match your environment, you can prevent unexpected failures during large or slow downloads, ensuring a smooth import process every time.
Removing Jest and unused dependencies
We've removed Jest and a few related dependencies from the codebase. They were no longer in use but they still lingered in our stack. Dropping them shrinks the overall dependency footprint and reduces the potential attack surface.
This cleanup doesn’t affect how you use Xen Orchestra, but it makes the project lighter and more secure behind the scenes.
Natural sorting for PIFs and VIFs
Physical interfaces (PIFs) and virtual interfaces (VIFs) are now sorted naturally. This means names like eth2 will appear before eth10, instead of being ordered alphabetically as plain text.
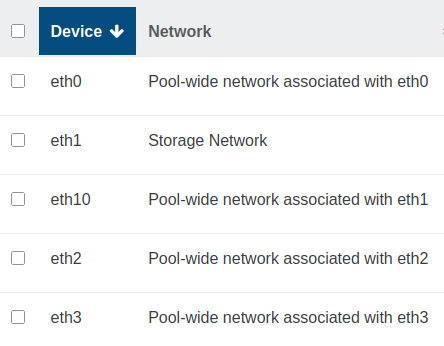
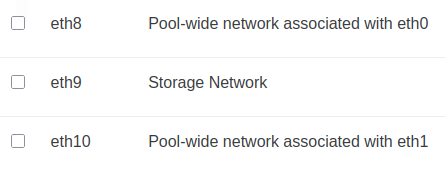
This small change makes scanning and selecting interfaces much more intuitive, especially when managing hosts with multiple NICs.
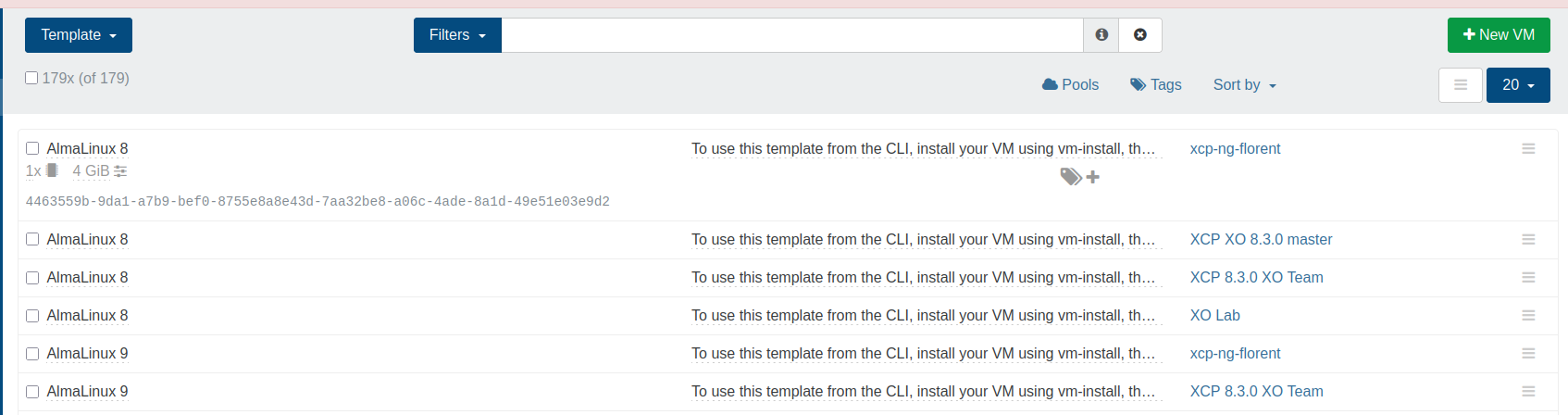
Template UUIDs visible in the list view
The template list now displays each template's UUID, next to its name. This makes it easier to find the exact template you’re working with , especially when many of the templates have similar names. This is small update will help you work faster, while minimizing mistakes.
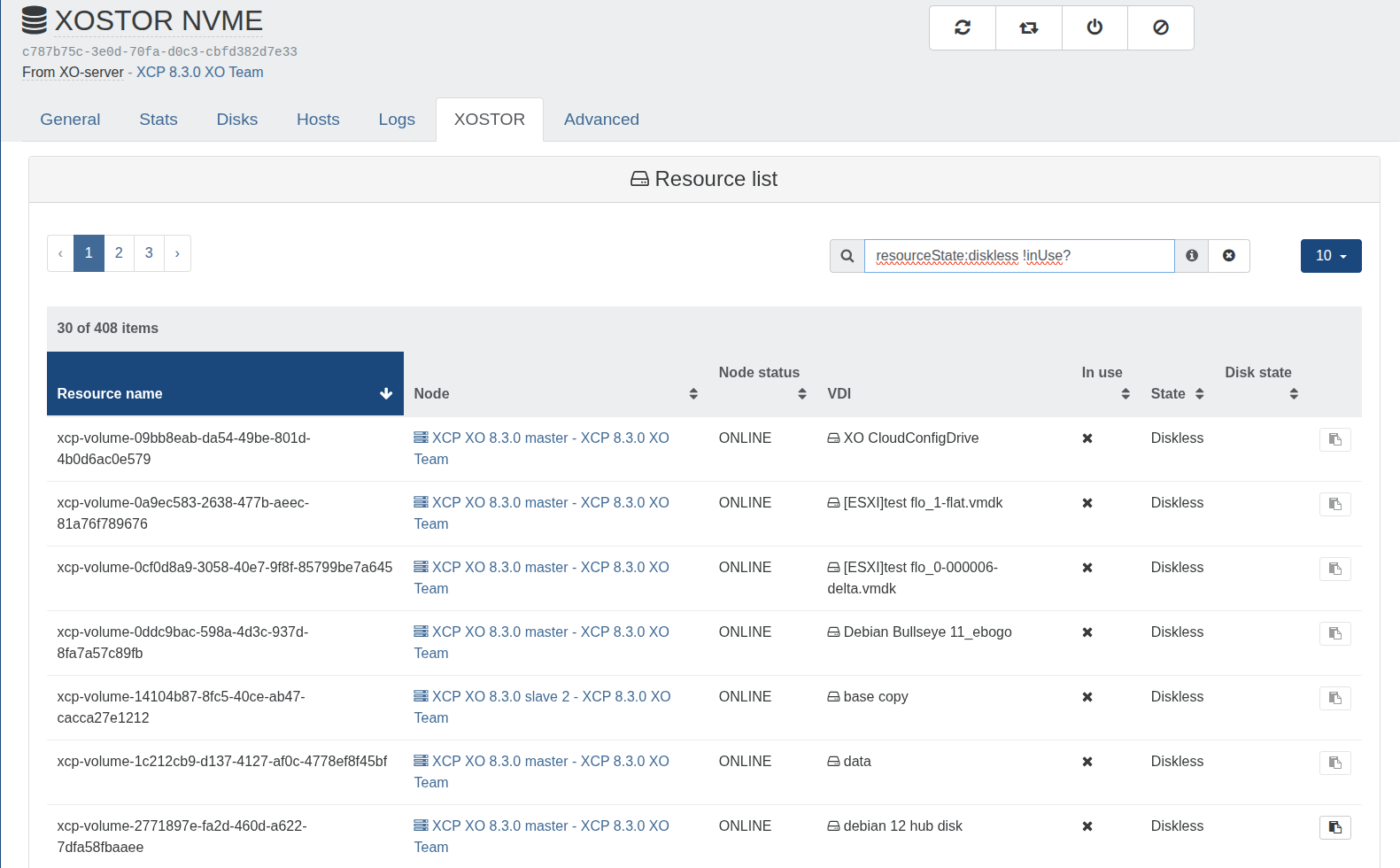
XOSTOR - Tie breaker status
XOSTOR now display resources without an associated volume. This includes tie-breaker and diskless ressources, which simplifies troubleshooting and advanced usage.